The Secure Memory Range from Nexus
When it comes to secure memory, we’ve got you covered.

CryptoAuthentication
Datakey CryptoAuthentication™ memory tokens and receptacles take Microchip’s ATSHA204A and ATECC608A high security hardware authentication ICs and repackage them into a rugged portable memory device.
Its features include a unique and non-changeable 72-bit serial number (set by Microchip), 512bit one-time programmable (OTP) zone, a random number generator, and a SHA-256 hash algorithm for data encryption.
Tokens can be used for the transfer of passwords (or other data needed for user authentication purposes) or for the physical transfer of security keys, certificates, sensitive data or system configuration files, as well as a secure credential in many other applications.
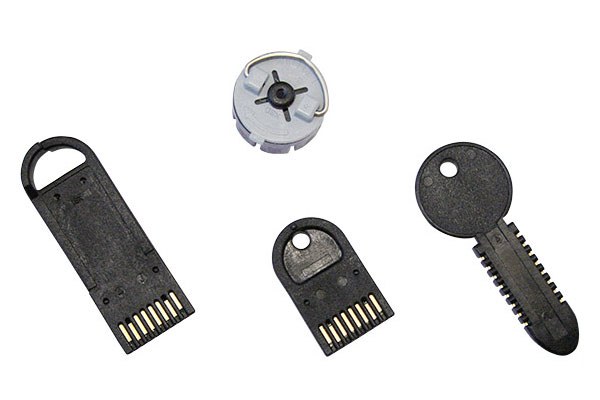
Datakey Serial Memory Tokens
Datakey serial memory products make it easy to add robust, portable memory to your embedded device.
We use industry-standard serial EEPROM, NOR Flash, USB Flash or SD and transform it into a rugged, portable unique form factor making it ultra secure.
Choose from capacities of 1 Kbit to 64 Mbits and serial interfaces including SPI, I2C and Microwire. You benefit from reduced time-to-market and virtually eliminate obsolescence concerns. Available in several form-factors, including the iconic key-shaped design, token or Bar – our most robust portable memory system.
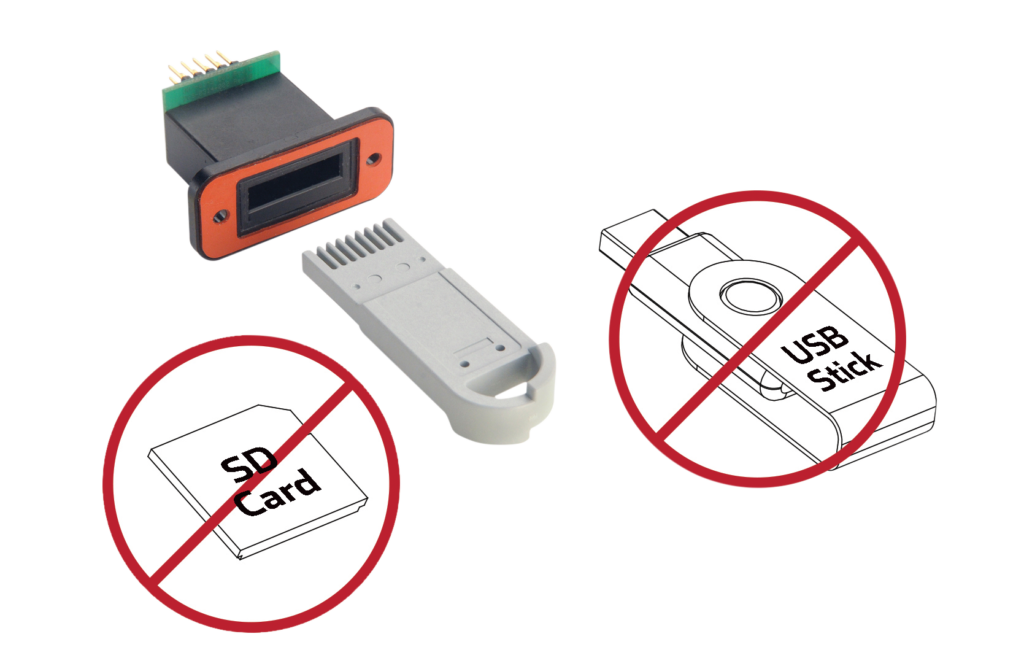
Datakey RUGGEDrive
Don’t send a fragile consumer device to do a RUGGEDrive™ token’s job.
When the going gets tough and the environment gets harsh, the RUGGEDrive™ line delivers USB flash drive or SD card functionality in an ultra-rugged form-factor with receptacles that withstand 33 times more insertion cycles than typical USB connectors and are available with an IP67 rating.
Due to the unique form factor of both the token and connector, your device’s data is kept secure. USB sticks and SD cards are not compatible with Datakey receptacles and if your Datakey token is misplaced, your data can not be accessed via a USB or SD port.

Flexxon WORM
Tamper proof data storage solutions using write-once-read-many technology. Flexxon WORM is increasingly being used in a whole variety of sectors – it protects sensitive data from deletion, modification and overwrites and in-built, unalterable data storage functions recognise the difference between a legal and an illegal action.
Illegal actions include trying to rename a directory or file, trying to delete a directory or file, trying to reformat the memory and trying to clone the device. Try any of those and the whole card goes into lockdown mode.
And because it’s implemented at the hardware and firmware level, WORM memory requires no software.
WORM memory is ideal if you have data that needs to be stored permanently without any changes – applications where it’s proved very useful include POS terminal hosts, voting machines and in financial transactions.
You can use Flexxon WORM memory in the form of your choice, including MicroSD, SD and USB.

Flexxon ROM
ROM (read only memory) is extremely popular at the moment – once the Read Only Mode is activated, any data stored either on a USB, SD, MicroSD or SSD is completely unalterable, no one can tamper with it, or change it.
We’re all familiar with CD-ROMs; this is the same concept, but in a modernised format.
In just a few minutes, the hardware can be set up, and the data is fully protected.
Increasingly, we’re seeing Flexxon ROM memory being used in the medical world to secure captured information, as well as government, finance and military applications.
Additionally, ROM would be well suited for use in embedded applications in IoT devices.

Flexxon X-MASK
Available in USB, MicroSD and SD, the X-Mask protects your data by:
• Making the drive invisible
• Granting access only through authentication
Once installed, the drive and the data can’t even be seen without the security tool AND password; without either of those things, the data remains hidden.
The X-MASK works by encrypting the data at the firmware and hardware level, using hash algorithms and data scrambling.
The security tool also protects from side channel attacks – because the security tool is required for authentication, side channel attacks are nullified.
The X-MASK can also be configured to only pair with specific devices, adding an additional layer of security, and it’s ideal for IoT devices that use MicroSD or SD cards that have sensitive information on.
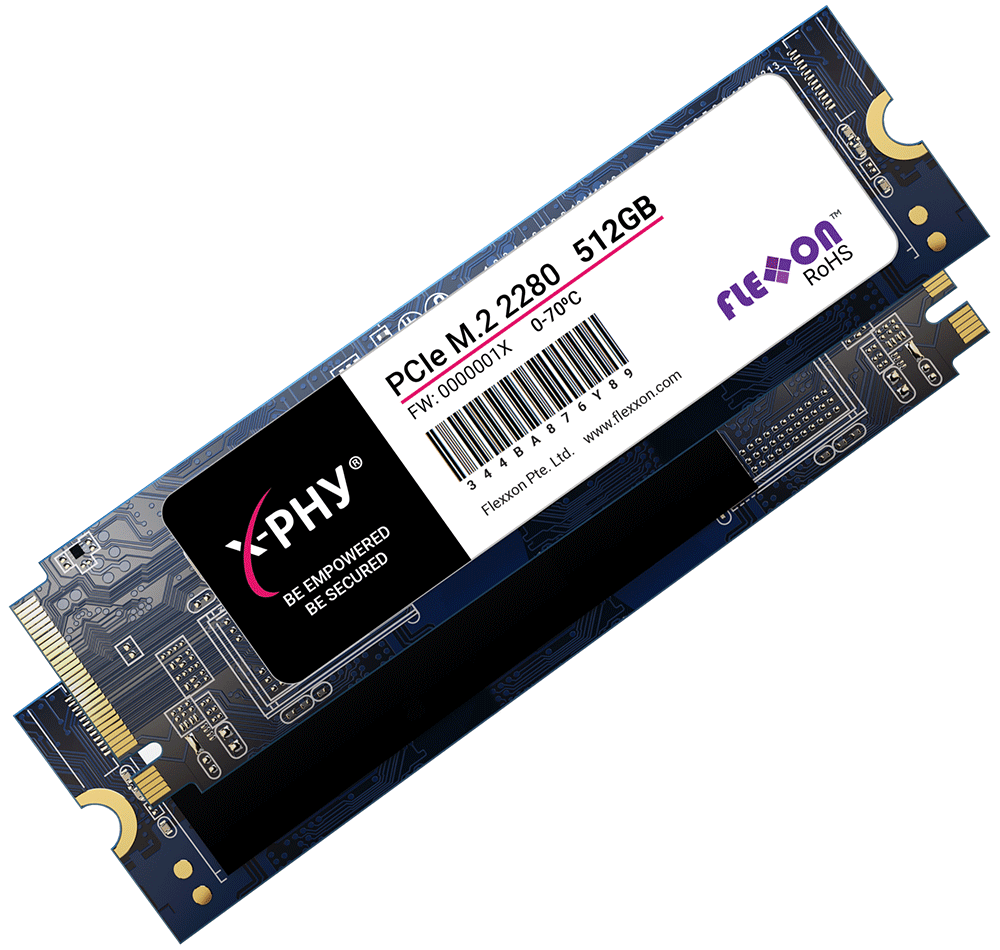
Flexxon X-PHY
The X-PHY uses low-level programming to analyse data access patterns and detect any harmful attempts to access your data using AI and machine learning. With security embedded in the SSD’s firmware closest to your valuable data. Flexxon’s industrial cyber security solutions offer real-time protection against zero-day vulnerabilities, and other unknown threats that may be able to bypass software-based cybersecurity systems.
Hardware sensors are also built on the SSD, protecting against physical threats like drive theft and other side-channel attacks. Essentially, it functions as a standalone machine that lives inside of your computer and gives you 24/7 cybersecurity protection.
High level security functions include:
- Data encryption
- Secure erase
- Write protection
This makes the X-PHY® a perfect all-in-one security product for data transfer and data storage.
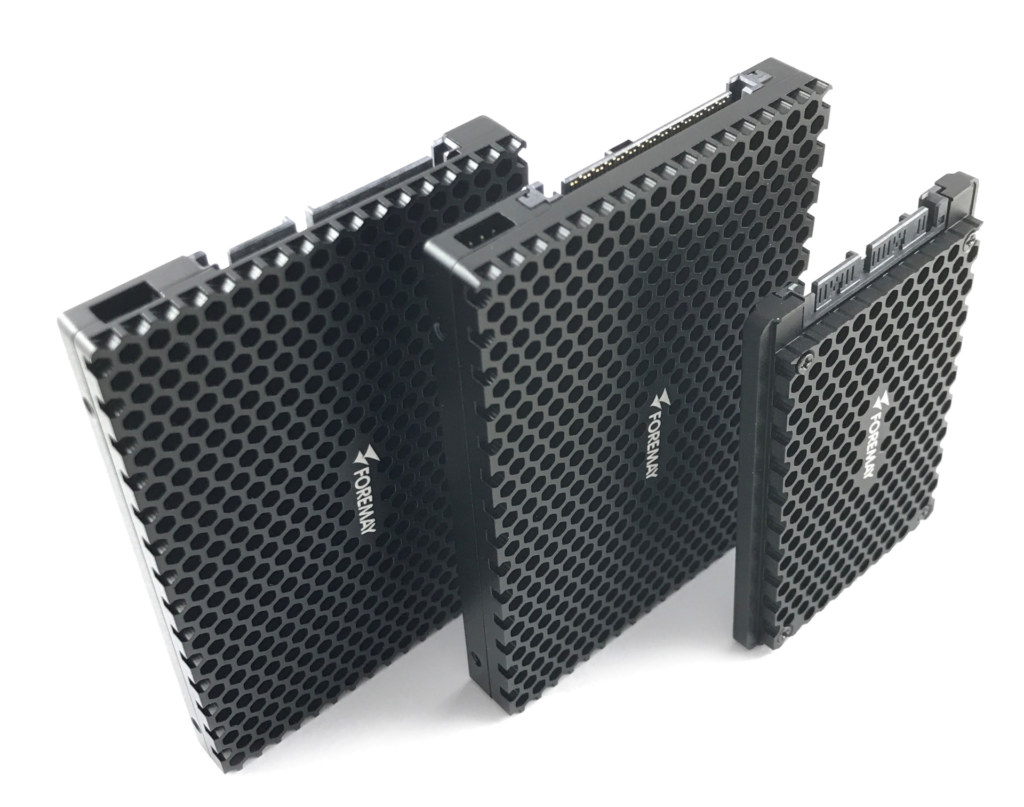
Foremay Ultra Rugged SSD
Foremay rugged military and space grade SSDs are designed for demanding applications in challenging environments. Their SSDs meet or exceed MIL-STD-810 F/G and their expertise in military secure erase solutions, advanced encryption technologies and ultra-wide operating temperatures make them an ideal choice for military, defence, aerospace, and deep space sectors. Foremay offer advanced security and complete solutions in military secure erase and self-destruction.
Features include:
- Optional rugged connectors with 100,000 mating cycles.
- Anti-radiation, anti-magnetic, anti-vibration
- Operating temperatures: -55~+125°C
- World’s Highest capacity SSDs
- Interfaces and form factors: SATA, mSATA. microSATA, NVMe U.2, M.2, half slim SATA, IDE, CF, CFast, PCIe, VPX, PXIe, Disk-on-Chip and customised interfaces.
- Extended EOL plans for long term supply
Peace of mind
For decades, organisations across Europe have been using – and continue to use – products recommended and supported by Nexus, and our customers have the peace of mind knowing that their memory solutions will stand up to the most extreme situations and remain secure.
Applications engineers at heart
Moreover, we are far more than distributors or resellers of memory products. We are applications engineers at heart. We have sound advice to offer and can work under terms of strict confidentiality. Also, such is the close relationship we enjoy with our suppliers, we can work with them to develop new solutions – see ‘Custom Products’.
To see how our products can help you to be 'secure by design' watch this video
Want to chat about our Secure Memory Range?
Call us now on +44 (0)1794 301439 or fill in the form below and we’ll come back to you ASAP.
